Fragile Watermark Is Used for Which Main Application
1 we know that a pixel fMj in Ni is chosen only when the wi and wj are different. Download Citation Construction Fragile Digital Watermark Used by a Team of Authors in Executable Files According to statistical research a violation of.

High Level Structure Of The Fragile Watermark Embedding Procedure Ih Download Scientific Diagram
Based on the analysis of the limitation of the text fragile watermark algorithm in the documents integrity authentication a kind of security system combining digital signature and the fragile watermark is proposed used the dual password authentication and the content authentication.

. The main application of fragile watermarks is in content authentication. A Fragile Digital Watermark Used to Verify the Integrity of Vector Map Abstract. A robust one and fragile one.
According to the invention a fragile watermark is provided in or in coding related to a buried data channel 40 42 44 46 provided in the audio samples of the media signal In this way the fragile watermark can be made to be very complex. The Application of Fragile Watermark in E-Governance. Fragile watermark implementation in Java.
What is Fragile Watermarking. Fragile Marking Applications A fragile watermark is a mark that is readily al-. Fragile watermarks are more easy to devise than robust ones and are usually applied in authentication scenarios.
These watermarks become invalid even if a slight modification is done to the watermarked image. Based on the analysis of the limitation of the text fragile watermark algorithm in the documents. The present invention is concerned with inclusion of a fragile watermark in an original printed document to aid in a determination whether a document under examination is an original or a copy.
In this paper we focus on the application of fragile watermark in e-governance security system. Comparison of proposed technique with existing fragile biometric techniques Encryption Maximum Watermarking Used Type of Size of host Type of Size of Technique of Application PSNR Domain Transform host image image Watermark Watermark watermark dB Wang et al. This class of watermarks provides selective robustness to a certain set of manipulations which.
The watermarking technology that makes the embedded information sensitive to any operations. So the watermark is not destroyed after some attacks and can easily detected to provide certification. Grayscale Integrity Not Spatial SVD 320280 Not used Binary 280 bits 2008 Iris.
Many important applications could benefit from the use of fragile watermarks. The methods of integrity authentication for vector maps were described at fist then digital watermarking for vector data was introduced. In this paper we focus on the application of fragile watermark in e-governance security system.
US7730037B2 US11250460 US25046005A US7730037B2 US 7730037 B2 US7730037 B2 US 7730037B2 US 25046005 A US25046005 A US 25046005A US 7730037 B2 US7730037 B2 US 7730037B2 Authority. The factor -1wj in Eq. Most of the work as reported in the literature in watermarking is in the area of robust techniques.
The watermark may be applied by making small tonal adjustments on a pixel block by pixel block basis in data used to generate the original document. Home Browse by Title Proceedings ICMECG 08 The Application of Fragile Watermark in E-Governance. Genetic-Algorithm-Based Optimization of Fragile Watermarking in Discrete Hartley Transform Domain Advances in Computational Intelligence and Robotics.
The method embeds two watermarks into media. Definition of Fragile Watermarking. This technology is suitable for content authentication.
We propose a method that increases the robustness of copyright protection watermarks by persuading users not to try attacking the watermark. Based on the analysis of the limitation of the text fragile watermark algorithm in the documents integrity authentication a kind of security system combining digital signature and the fragile watermark is proposed used the dual password authentication and the content authentication the security of important documents transmission been greatly enhanced in e-governance. Authors Info Claims.
The aims of such photo watermarks are completely different. The main application area for digital watermarking is copyright protection. The present invention relates to methods devices a signal and recorded medium relating to a fragile watermark WM in a media signal.
In this case the watermarks are designed to be vulnerable to all modifications ie they become undetectable by even the slightest host data modification. Contribute to rmkaneFragileWatermark development by creating an account on GitHub. A kind of security system combining digital signature and the fragile watermark is proposed used the dual password authentication and the content authentication the security of important documents transmission been greatly enhanced in e-governance.
The binary watermark w is used as a selection determinant. Quality of the image does not suffer much it can be used in almost all the applications Latha et al 2007. From the XOR operation in Eq.
In this paper we focus on the application of fragile watermark in e-governance security system. Involving the watermark bits unknown to the third party in Eq. 1 determines whether fMj is to be added to or subtracted from Si.
According to the invention a fragile watermark is provided in or in coding related to a buried data channel 40 42 44 46 provided in the audio samples of the media signal In this way the fragile watermark can be made to be very complex. The present invention relates to methods devices a signal and recorded medium relating to a fragile watermark WM in a media signal. A semi-fragile watermark is a mark which is highly sensitive to a modification of the stego-medium.
Definition of Fragile Watermarks. A fragile watermarking software scheme should be able to detect any change in the signal and identify where it has taken place and possibly what the signal was before modification. 22 DIVISION BASED ON APPLICATIONS Based on application watermarks are sub-divided into fragile semi-fragile and robust watermarks.
It serves at proving the. It is mainly used to prevent various noisy attacks geometrical or non-geometrical attacks without tampering embedded wa-termark. Fragile 221 FRAGILE WATERMARKS These watermarks are very sensitive.

My Wife Isn T Fragile Like A Flower Funny Shirt Classic Round Sticker Zazzle Com In 2020 Happy Father Day Quotes Fathers Day Quotes Funny Fathers Day Quotes

Schematic Diagram Of A Fragile Watermarking Authentication System Download Scientific Diagram

Fine Grain Watermarking The Watermark Computed As The Hash Of The Download Scientific Diagram
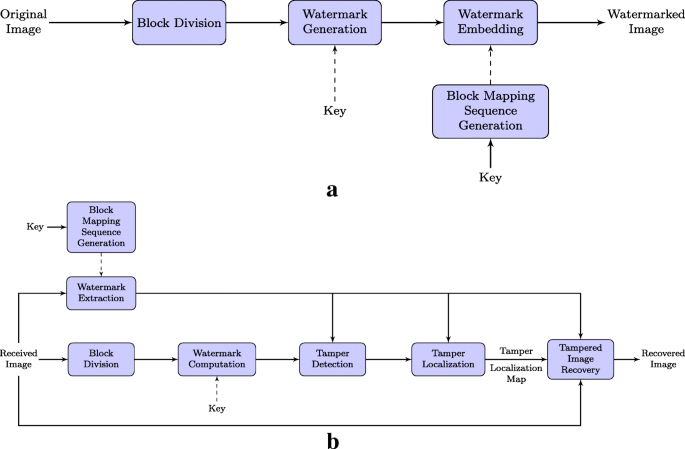
A Survey On Fragile Watermarking Based Image Authentication Schemes Springerlink
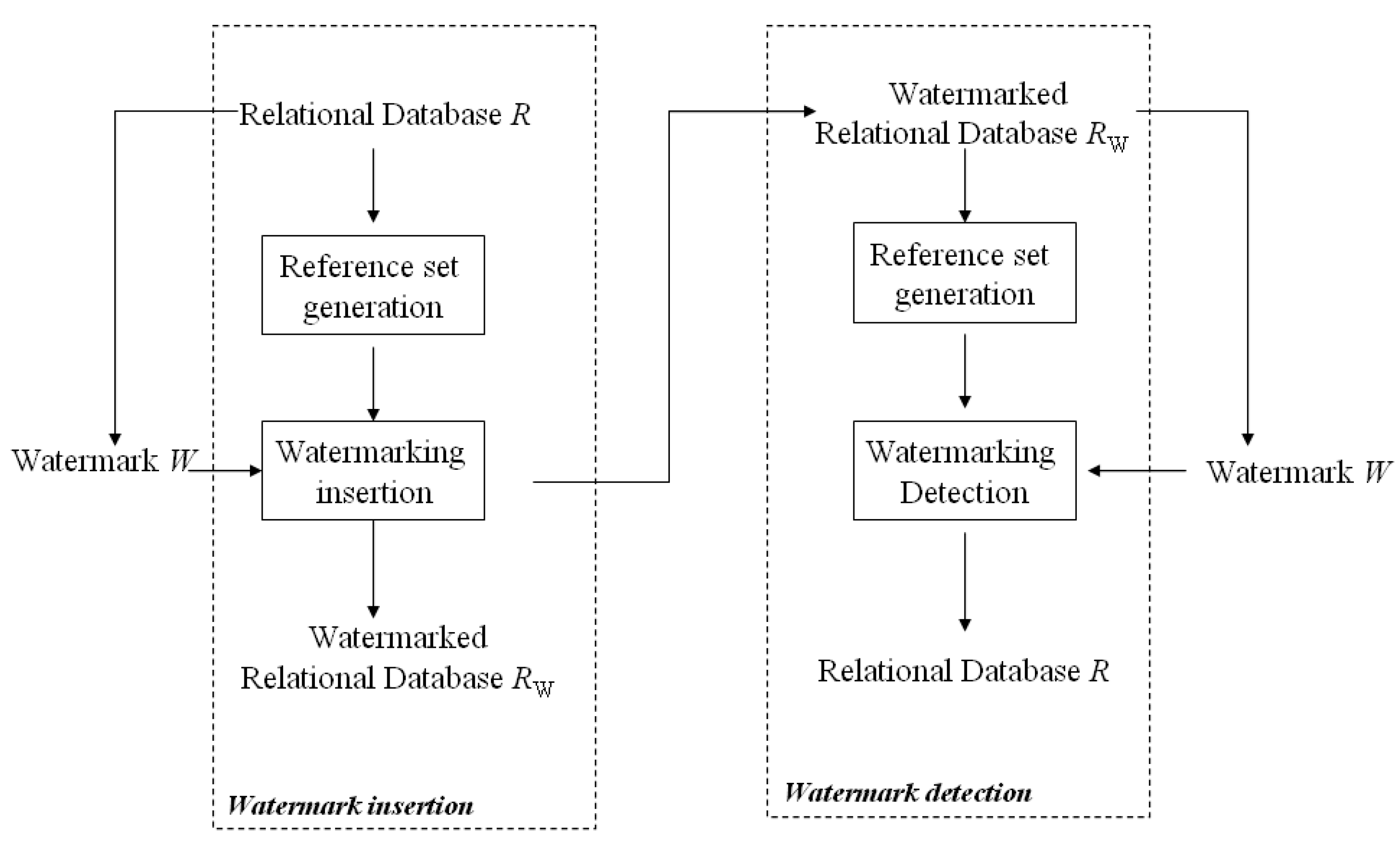
Symmetry Free Full Text Lrw Crdb Lossless Robust Watermarking Scheme For Categorical Relational Databases Html

Happy Easter Bunny Face Digital Download Svg Png Jpeg Dxf Etsy In 2022 Happy Easter Bunny Bunny Face Happy Easter

Watermark Extraction Method Download Scientific Diagram

Results Of Legal And Illegal Watermark Removal Images A And B Are Download Scientific Diagram

A The Original Image And B The Embedded Watermark C The Download Scientific Diagram

Image Shared By Rubyaes Find Images And Videos About Kpop Aesthetic And Themes On We Heart It The App To G Anime Art Girl Aesthetic Themes Aesthetic Anime
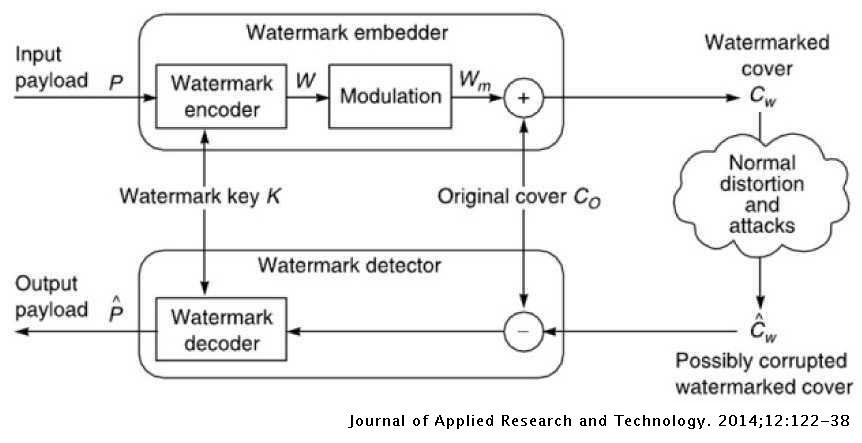
Robust Image Watermarking Theories And Techniques A Review Journal Of Applied Research And Technology Jart
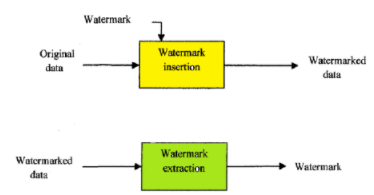
Visible Watermark For Secure Credential Website Page By Ashadi Sedana Pratama Dana Product Tech Medium
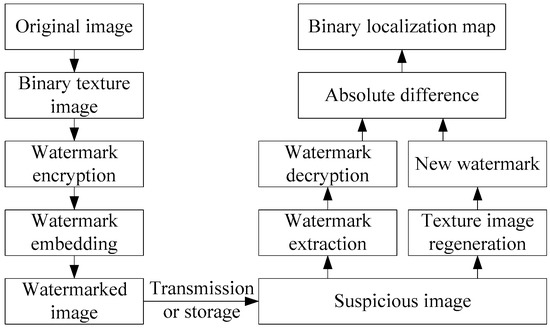
Algorithms Free Full Text Fragile Watermarking For Image Authentication Using The Characteristic Of Svd Html
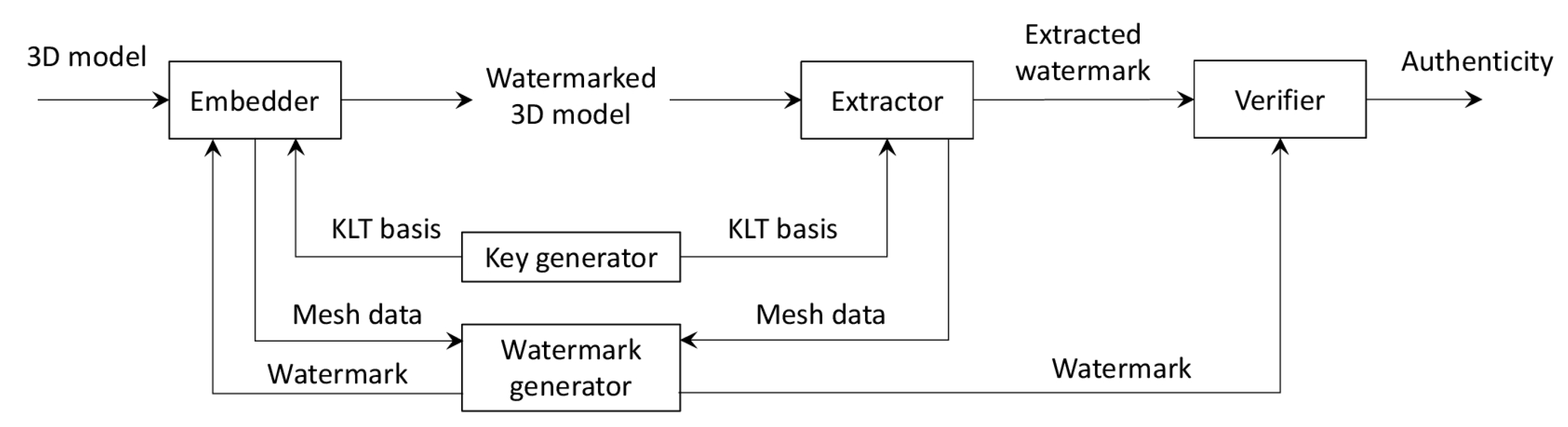
Applied Sciences Free Full Text Fragile Watermarking Of 3d Models In A Transformed Domain Html
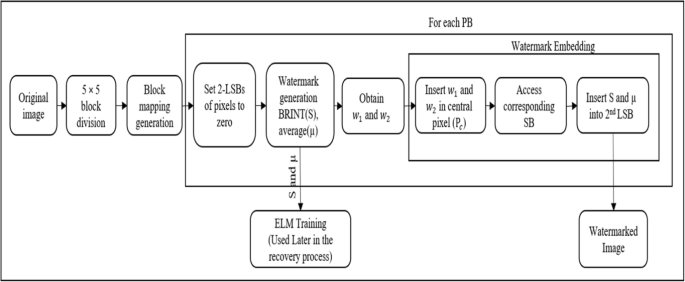
Fragile Watermarking For Image Authentication Using Brint And Elm Springerlink



Comments
Post a Comment